Introduction
Lag and Crash CTF 2023 took place from the 14th to 16th of April. Despite being one of the highlights of the polytechnic CTF scene, due to other commitments I'd never actually joined as a player until this year.
For this CTF, I was reunited with a few Nanyang Polytechnic schoolmates under my friend Gabriel's team 'dad'. Our lineup was:
- Gabriel Seet
- Yeo Jong Han
- Derrick Png
- Mark Bosco (me!)
We finished in first place with a narrow 12 point lead (25742 points to 25730). I guess my teammates were justified in not letting me buy too many hints, haha.
In addition to 48 hours of CTF fun, each of us won $500 and an Offensive Security Learn Fundamentals subscription, plus some cool swag. All in all, a weekend well spent.
Although there were many interesting challenges during the CTF, there are a few reasons why I've decided to do a detailed writeup for this particular one:
- Like most forensics challenges, this is essentially a 'white-box' challenge: all information required to find the flag is provided upfront. With the right deductions, the experienced player can efficiently complete the challenge without spending unnecessary time on blind enumeration (as is the case with certain 'black-box' web and pwn challenges). Therefore, the thought process and tools shown here may be readily transferred to other similar challenges.
- Although the challenge could be solved using only standard disk forensics techniques, the software set-up and contextual knowledge required to effectively approach the challenge might have been a hurdle to new players. Full disk forensics challenges are relatively rare in most CTFs (due to the large files required), so writeups are less common. By providing a thorough walkthrough, I hope more players will be interested to explore this "blue-team" side of CTFs and cybersecurity.
So here you are, this is my Licensed Forensics walkthrough for LnC 2023.
Challenge Info
Name: Licensed Forensics
Category: Forensics
Difficulty: Medium (9 solves out of 87 teams)
Challenge Creator: Hoe Ming Wei
Challenge description:
We have a rogue forensics investigator who got away with our files and documents! Fortunately, they were not able to destroy all evidence before their escape from the compound. We have confiscated his computer and created an image of one of his drives. It is up to you to figure out what he is hiding.
p.s. Please be careful and do not unintentionally change your main system settings.
Link to challenge files:
https://drive.google.com/file/d/12dN8gxb653xAJsEzXQp3eZMXxIWkhMjI/view?usp=sharing (Suspect Image.E01)
https://drive.google.com/file/d/12dN8gxb653xAJsEzXQp3eZMXxIWkhMjI/view?usp=sharing (Suspect Image.E01)
Setup
Before we start working on the challenge, we must find a way to view the contents of Suspect Image.E01 (the "image of one of his drives" referenced in the challenge description).
E01 stands for (EnCase image file), and is just one of many possible disk image formats. An image of a disk is an exact, identical copy of the contents of a physical medium, such as a thumb drive or a hard disk. They're often made during the digital forensics process. This ensures the investigator can work freely with the imaged copy without accidentally altering the original evidence.
Outside of cybersecurity, they can be used to create exact copies of a PC's disks. You often see this being done in computer labs over the holidays.
For more information about imaging a disk (helpful if you want to create a filesystem forensics challenge), check out this article.
One common way of investigating an E01 is to mount it directly. This makes the file show up as a physical drive on your computer (like a real hard disk might).
An example of a E01 file being mounted directly. Image taken from https://dfirmadness.com/mounting-case001-e01-files/. Check out the article for the full instructions on how to do this,
On the other hand, many professional digital forensics investigators would prefer to use a forensics software suite. These tools offer advanced viewing, searching, and file extraction features.
One of the most popular options is EnCase Forensic, which has been used in real-life court cases. This was also tool we used in school during the cyber forensics module. It's a rather expensive tool, though, usually out of reach for the hobbyist CTF player.
The EnCase interface, as seen in their product overview.
A popular alternative is Autopsy, which is free and open source. In the CTF context, the two tools are mostly similar, and which one you choose is a matter of personal preference (and budget). Another reason I use Autopsy is that it is included as part of Flare VM. (If you do not already have a Flare VM instance, I highly encourage you to give it a go. It is to blue teaming what Kali Linux is to red teaming.)
This walkthrough will be done in Autopsy, since it is available to everyone for free, but as the techniques and process are universal, EnCase users should also be able to follow along.
Preparing the case
Once you have your preferred forensics tool installed, the next step is to import the evidence file (Suspect Image.E01).
After opening Autopsy, you will be prompted to create a new case.
Fill up the case information and create the case.
After the case is created, you will be prompted to add a Data Source. For this challenge, we are adding a Disk Image.
Select the evidence file to import. While not crucial to this challenge, setting the right time zone is sometime necessary to correlate actions from different sources.
Select some Ingest Modules! These are one highlight of using dedicated forensic software. They can automatically find encrypted content, email addresses, and even hidden files. The important ones for this challenge are "Encryption Detection" and "Keyword Search".
The E01 file has been imported.
If this is your first time using Autopsy, I recommend checking out the official user documentation on the different data types.
Now that we're all set up, let's get to finding some flags!
Solving the challenge
For longer challenges with multiple steps, I usually repeat a three-step process:
- Observe: What is interesting, unusual, or surprising?
- Deduce: What could this mean?
- Confirm: What my guess correct? What new information have I obtained?
This helps me maintain a structure for any action I take, and also lets me get help and suggestions from my teammate if I get stuck.
Diagram of the three-step CTF process, from my Introduction to CTF workshop slides.
At the highest level, a storage medium is divided into partitions. You can think of the storage medium as a cake, and the partitions are individual slices. If you're interested to learn more about different partition types, this Wikipedia article covers the basics.
After opening Suspect Evidence.E01, we can see that there are four partitions. Apart from the number of partitions, we can also see each partition's type (highlighted in green), as well as the size (highlighted in pink).
For your interest, the four partitions are a result of a Windows installation. This article explains the installation and partition creation process in greater detail.
However, knowing this is not necessary to solve the challenge. Only vol5 contains any files.
Click the '+' icon to the left of the volume name to expand the volume. Vol1, vol4 and vol6 contain no subdirectories
Screenshot from of the main hard disk of a Windows computer.
If you're a Windows OS user, these folders should look familiar. The main hard disk of Windows computers have a few standard folders. The important ones to take note of are:
- Program Files: Contains executable programs (software) for all users to use. For example, Google Chrome.
Program Files (x86) serves the same purpose, but contains programs using a different architecture. This Microsoft Blog post explains the specifics.
Spoiler alert: this folder is not present on Suspect Image.E01. Find out why at the end of this article. - Users: Contains the files belonging to each Windows user on the computer. If you've ever had to share a computer, you'll know that everyone can have their own account. This keeps everyone's documents nicely separated, and more importantly, private.
- Windows: This contains important system files, usually managed by the operating system itself. It's also a forensic investigator's treasure trove, containing logs of system activity and other user settings.
- $RECYCLE.BIN: As the name suggests, this contains files placed in the Windows recycle bin. Helpful for some challenges; but not for this one.
Normally, I might start by looking through a few folders at random, noting down anything that seems suspicious. For this challenge, however, the Encryption Detection module automatically found an encrypted file.
The details pane shows the full path of flag.zip (both files are identical).
Rather than searching for the file manually, right click the row and select "View Source File in Directory" to jump to the file's parent folder directly.
We can see that the encrypted flag.zip file is in the Desktop folder of the user Evil_Forensigator. This confirms that the file is relevant to the challenge, as the challenge description referenced a "rogue forensics investigator".
The flag.zip was found in another zip folder, Secret_Documents.zip. Looking through this folder, the only other file that stands out is Note.txt.
Note to self, do not let the authorities look in the contents of my secret folder.
The password for the secret folder is:
32***9*********9***
Whoops, spilled my digital tea on the password! I can't remember my password...
Eh, no worries, I keep my password backed up somewhere else. Gotta remember that my
virtual machine LICENSE is the KEY. It's important..!
Yes... The KEY...
From this file, we can make a three deductions:
- Flag.zip is indeed encrypted
- The password is of the format "32***9*********9***", where "*" represents any character
- The password is backed up on the disk provided, and associated with a virtual machine license key
At this stage, there are two possible solutions:
- You could brute-force every possible combination to guess flag.zip's password and retrieve the flag. That is, if you have access to some special supercomputer.
- For everyone else using a regular computer, we will have to look for the Virtual Machine license key, and hope that leads to the zip file password.
On Windows computers, the main virtual machine software used is:
- Oracle VirtualBox, which is free.
- VMWare Workstation, which required a paid subscription.
It is therefore more likely that the "virtual machine license key" refers to a VMWare Workstation license key specifically.
Interestingly, a VMWare Workstation license usually consists of 25 characters, separated by dashes (e.g. ABCDE-12345-ABCDE-12345-ABCDE). This is markedly different from the password format in Note.txt (32***9*********9***).
Time for some quick Googling!
This official VMWare article, though quite old, lets us deduce that the VMWare Workstation can be found in the Windows Registry, under the path "SOFTWARE > Wow6432Node > VMware, Inc. >VMware Player".
if you're not familiar with the registry, it's a set of database files used by the Windows OS, usually to record user preferences and system information. I recommend this Wikipedia article for a full explanation.
Though the VMWare article recommends the use of the 'regedit' tool, if we were to run the tool directly, we would be looking at the registry of our own machine, not the registry of the E01 challenge file.
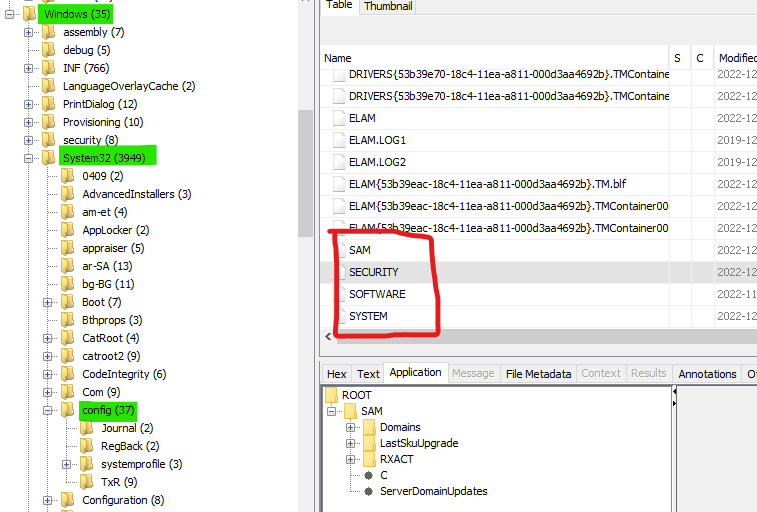
Luckily for us, the registry is made up of a few different files, stored in the "Windows\System32\config\" folder. We can access the contents of the registry files directly using Autopsy.
From the article above, we know we need the SOFTWARE subkey. However, this file is blank!
Zeros all the way; Horror of horrors!
At this point, it would have been easy to abandon all hope, and start going through folders at random in search of the missing SOFTWARE registry file. The file might have been renamed, hidden within another file, or otherwise
Luckily, Autopsy's ingest modules come to the rescue again. Earlier, the Keyword Search module we used extracted text from files and added them to a searchable index.
Since we know the registry path contains the text "VMware, Inc.", I ran a search using that as a keyword.
You can find the Keyword Search function at the top-right corner of Autopsy.
The keyword search returns a very long list of files, so I sorted them by filetype (MIME type).
There were only three Windows registry files, and one of them was named SOFTWARE-slack.
We're getting close!
Unlike the previous SOFTWARE file found, this one contains actual data. Time to see if it contains the VMWare Workstation license key. To check, go to WOW6432Node > VMWare, Inc. > VMWare Workstation
Interesting! Instead of a proper license key, the registry key contains a link: https://pastebin.com/F6j80vMC.
The Pastebin link contains another note:
Good thing that I kept a backup!
AGH I SPILT THE DIGITAL TEA™ AGAIN
**983*432689537*123
Our search is at an end. By combining the two parts of the password (32***9*********9*** from Note.txt and **983*432689537*123 from the Pastebin link), we can construct the password for flag.zip. The password is 3298394326895379123.
Extra credit: Other points of interest
While looking for the flag, I pursued several other points of investigation that ultimately yielded no results. However, these "wrong paths" might end up being important in future CTFs, so keep an eye out for them!
- Windows Event Log files (\Windows\System32\winevt\Logs). Windows Event Logs contain tons of information about the system: when users log on, which processes are running, and even commands entered by users. Event logs have the ".evtx" extension, and can be viewed with the built-in Event Viewer application.
- RegBack folder (\Windows\System32\config\RegBack). This folder sometimes contains backups of registry files. You can find more information about registry backups in this guide.
- VMware Workstation logs (\Windows\Temp). This folder contains temporary files, and contains miscellaneous information that is sometimes very valuable. contained several VMWare logs associated with the Evil_Forensigator user.
Special Feature: Interview with the challenge creator
As an occasional CTF creator and organizer myself, I'm always curious about how each challenge was put together behind the scenes. Here is a short QnA with the Ming Wei, who created this challenge.
What was the inspiration for this challenge?
I was trying to find the license key of the VMWare Workstation for my classmate to activate his software (checking the registry information seemed to be the most reliable). I happened to think that changing or hiding information in the registry might be a fun way to hide information.
I used PasteBin because I thought it would be more fun for the participants to have a few extra steps to solve the puzzle (I figured adding some easy steps in the challenge might make them feel that they accomplished more)
The SOFTWARE file being blank was not really what I intended, just a byproduct of how I created the environment for the imaging.
Why did you give this challenge a 'medium' difficulty?
I thought my challenge maybe could be classified as "medium" if the "easy" challenges were the base64/etc challenges.
I believe it would have been very much solvable by most people if they had more time. It was unfortunate that this challenge was released in the last wave.
How did you create the actual E01 file for the challenge?
I built everything in a VM and used FTK to create the E01 file. I wanted to make sure that the size of the evidence file was not too big. So I figured that deleting some of the system files (not important to solving the CTF challenge) can simulate the imperfect evidence you may get in a real world setting as well as reducing file size.
There wasn't any particular challenge that I was faced with. Maybe some kinks that were easily googled.
What's one thing you hope players learnt after attempting your challenge?
Most things can be solved with Google and time.
Most things can be solved with Google and time.
Acknowledgements
Thanks to my teammates from 'dad' being in this together, and offering bits of advice in our Discord chat as I worked on this challenge.
I would also like to thank the organizers of Lag and Crash CTF 2023 (who also worked very hard to have a physical event on the last day).
Finally, many different groups came together to sponsor this CTF. You can find out more about them here: https://lagncra.sh/#sponsors.
Update: Got my medal!